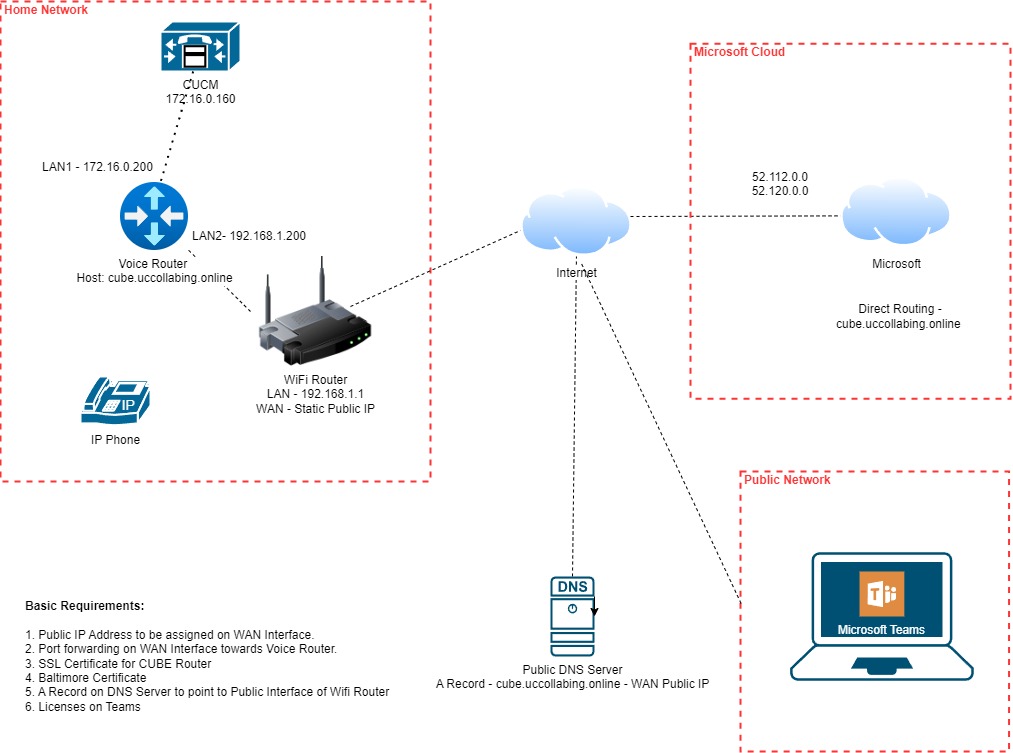
Microsoft Teams Direct Routing with Cisco CUBE
Microsoft Teams Direct Routing is a feature that enables organizations to connect their on-premises telephony systems to the Microsoft Teams platform, allowing Teams users to make and receive calls to and from the public switched telephone network (PSTN). This functionality is essential for companies looking to leverage Teams for voice communications while maintaining their existing telephony infrastructure.
Cisco’s Cloud Unified Border Element (CUBE) serves as a critical component in this setup. CUBE acts as a gateway between the Microsoft Teams cloud service and the on-premises PSTN or SIP-based telephony systems. It handles the SIP signaling, media routing, and ensures security and interoperability between Teams and traditional telephony systems. The integration provides voice quality monitoring, call routing, and encryption for secure communications.
Cisco CUBE supports key features like call admission control, number translation, and support for various codecs, ensuring that Teams users have a seamless communication experience. Additionally, it enables high availability with features like load balancing and fault tolerance.
For businesses that require a robust and scalable telephony solution, Microsoft Teams Direct Routing combined with Cisco CUBE offers a reliable solution for integrating cloud-based communication with existing telephony systems, delivering cost savings and flexibility in a modern collaboration environment.
In this article, we will configure Cisco CUBE direct routing with Microsoft Teams. Here is a detailed video and configuration guide.
Configuration on Cisco CUBE
Let’s first do the CA Certificate like Root/Intermediate, Baltimore and DigiCert + Host Certificate CSR generation and Installation.
ip domain name uccollabing.online ! Sets the domain name for the device. This is important for generating certificates and other domain-related services. crypto key generate rsa general-keys label CUBE-RSA-KEY modulus 2048 exportable ! Generates an RSA key pair with a label `CUBE-RSA-KEY`, a key size of 2048 bits, and makes the key exportable. This key will be used for SSH and certificate purposes. ip ssh rsa keypair-name CUBE-RSA-KEY ! Specifies the RSA key pair to be used for SSH, using the previously generated key pair `CUBE-RSA-KEY`. crypto pki trustpoint CUBE-CERT-STORE enrollment terminal fqdn cube.uccollabing.online subject-name cn=cube.uccollabing.online,OU=IT,O=UCCollabing subject-alt-name cube.uccollabing.online serial-number none ip-address none revocation-check none rsakeypair CUBE-RSA-KEY ! Creates a trustpoint named `CUBE-CERT-STORE` with terminal enrollment. Specifies the FQDN, subject name, and alternate name for the certificate. Uses the RSA key pair `CUBE-RSA-KEY`. crypto pki enroll CUBE-CERT-STORE ! Enrolls the trustpoint `CUBE-CERT-STORE` to generate a certificate request. crypto pki authenticate CUBE-CERT-STORE ! Authenticates the trustpoint `CUBE-CERT-STORE` to import the CA certificate. crypto pki import CUBE-CERT-STORE certificate ! Imports the certificate for the trustpoint `CUBE-CERT-STORE`. sip-ua crypto signaling default trustpoint CUBE-CERT-STORE ! Configures SIP UA to use the default trustpoint `CUBE-CERT-STORE` for securing signaling. ip http authentication local ip http secure-server ip http secure-trustpoint CUBE-CERT-STORE !Configures HTTP authentication to use local credentials, enables the secure HTTP server, and specifies the trustpoint for secure HTTP connections as "CUBE-CERT-STORE". crypto pki trustpoint BALTOMORE-MICROSOFT-CA enrollment terminal revocation-check none ! Creates a trustpoint named `BALTOMORE-MICROSOFT-CA` with terminal enrollment and no revocation check. crypto pki authenticate BALTOMORE-MICROSOFT-CA ! Authenticates the trustpoint `BALTOMORE-MICROSOFT-CA` to import the CA certificate. crypto pki trustpoint DIGICERT-MICROSOFT-CA enrollment terminal revocation-check none ! Creates a trustpoint named `DIGICERT-MICROSOFT-CA` with terminal enrollment and no revocation check. crypto pki authenticate DIGICERT-MICROSOFT-CA ! Authenticates the trustpoint `DIGICERT-MICROSOFT-CA` to import the CA certificate.
Let’s do rest of the configuration related to Teams and CUCM on the CUBE
voice class srtp-crypto 1 crypto 1 AES_CM_128_HMAC_SHA1_80 ! This defines the SRTP encryption settings for secure RTP. AES_CM_128_HMAC_SHA1_80 is the selected cipher suite. voice class uri 290 sip host cube.uccollabing.online ! This defines the URI for a SIP host used for communication. In this case, the host is "cube.uccollabing.online" voice class uri CUCM sip host ipv4:172.16.0.160 ! This defines another URI for a SIP host, this time pointing to a Cisco Unified Communications Manager (CUCM) with IP address 172.16.0.160. voice class sip-hdr-passthrulist 290 passthru-hdr Referred-By ! This configuration allows the "Referred-By" SIP header to pass through without modification, ensuring proper call handling. voice class e164-pattern-map 200 e164 #9180101010.. ! This defines an E.164 pattern map. The pattern #9180101010.. allows the specified dialing pattern. voice class e164-pattern-map 1 e164 +911... ! Another E.164 pattern map for the pattern +911..., used for dialing numbers in the specified format. voice service voip ip address trusted list ipv4 52.112.0.0 255.252.0.0 ipv4 52.120.0.0 255.252.0.0 ipv4 172.16.0.0 255.255.255.0 ipv4 192.168.1.0 255.255.255.0 rtcp keepalive rtp-port range 16384 16386 address-hiding mode border-element allow-connections sip to sip no supplementary-service sip refer supplementary-service media-renegotiate fax protocol t38 version 0 ls-redundancy 0 hs-redundancy 0 fallback none sip session refresh header-passing error-passthru pass-thru headers 290 sip-profiles inbound srtp-crypto 1 !Configures VoIP service with trusted IP address list, RTCP keepalive, RTP port range, address hiding, SIP-to-IP connections, T.38 fax protocol, session refresh, header passing, and SRTP encryption. voice class codec 1 codec preference 1 g711ulaw codec preference 2 g711alaw codec preference 3 g729r8 codec preference 4 g729br8 ! !Configures codec preferences with G.711 uLaw, G.711 aLaw, G.729r8, and G.729br8 in voice class 1. ! voice class sip-profiles 200 rule 10 request ANY sip-header Contact modify "@.*:" "@cube.uccollabing.online:" rule 20 response ANY sip-header Contact modify "@.*:" "@cube.uccollabing.online:" rule 30 request ANY sip-header SIP-Req-URI modify "sip:(.*):5061 (.*)" "sip:\1:5061;user=phone \2" rule 40 request ANY sip-header User-Agent modify "(IOS.*)" "\1\x0D\x0AX-MS-SBC: Cisco UBE/ISR4321/\1" rule 50 response ANY sip-header Server modify "(IOS.*)" "\1\x0D\x0AX-MS-SBC: Cisco UBE/ISR4321/\1" rule 60 request ANY sdp-header Audio-Attribute modify "a=sendonly" "a=inactive" rule 70 response 200 sdp-header Audio-Connection-Info modify "0.0.0.0" "49.207.248.64" rule 71 response ANY sdp-header Connection-Info modify "IN IP4 192.168.1.200" "IN IP4 49.207.248.64" rule 72 response ANY sdp-header Audio-Connection-Info modify "IN IP4 192.168.1.200" "IN IP4 49.207.248.64" rule 73 request ANY sdp-header Connection-Info modify "IN IP4 192.168.1.200" "IN IP4 49.207.248.64" rule 74 request ANY sdp-header Audio-Connection-Info modify "IN IP4 192.168.1.200" "IN IP4 49.207.248.64" rule 80 request ANY sdp-header Audio-Attribute modify "(a=crypto:.*inline:[A-Za-z0-9+/=]+)" "\1|2^31" rule 90 response ANY sdp-header Audio-Attribute modify "(a=crypto:.*inline:[A-Za-z0-9+/=]+)" "\1|2^31" rule 100 request ANY sdp-header Audio-Attribute modify "a=candidate.*" "a=label:main-audio" rule 110 response ANY sdp-header Audio-Attribute modify "a=candidate.*" "a=label:main-audio" rule 120 response 486 sip-header Reason modify "cause=34;" "cause=17;" rule 300 response ANY sdp-header Audio-Attribute modify "a=rtcp:(.*) IN IP4 192.168.1.200" "a=rtcp:\1 IN IP4 49.207.248.64" rule 310 request ANY sdp-header Audio-Attribute modify "a=rtcp:(.*) IN IP4 192.168.1.200" "a=rtcp:\1 IN IP4 49.207.248.64" rule 320 response ANY sdp-header Audio-Attribute modify "a=candidate:1 1(.*) 192.168.1.200 (.*)" "a=candidate:1 1\1 49.207.248.64 \2" rule 330 request ANY sdp-header Audio-Attribute modify "a=candidate:1 1(.*) 192.168.1.200 (.*)" "a=candidate:1 1\1 49.207.248.64 \2" rule 340 response ANY sdp-header Audio-Attribute modify "a=candidate:1 2(.*) 192.168.1.200 (.*)" "a=candidate:1 2\1 49.207.248.64 \2" rule 350 request ANY sdp-header Audio-Attribute modify "a=candidate:1 2(.*) 192.168.1.200 (.*)" "a=candidate:1 2\1 49.207.248.64 \2" ! voice class sip-profiles 290 rule 10 request REFER sip-header From copy "@(.*com)" u05 rule 15 request REFER sip-header From copy "sip:(sip.*com)" u05 rule 20 request REFER sip-header Refer-To modify "sip:\+(.*)@.*:5061" "sip:+AAA\1@\u05:5061" rule 30 request REFER sip-header Refer-To modify "<sip:sip.*:5061" "<sip:+AAA@\u05:5061" rule 40 response ANY sip-header Server modify "(IOS.*)" "\1\x0D\x0AX-MS-SBC: Cisco UBE/ISR4321/\1" rule 50 request ANY sdp-header Audio-Attribute modify "a=ice-.*" "a=label:main-audio" rule 60 request ANY sdp-header Attribute modify "a=ice-.*" "a=label:main-audio" rule 70 response ANY sdp-header Audio-Attribute modify "IN IP4 49.207.248.64" "IN IP4 192.168.1.200" rule 80 request ANY sdp-header Connection-Info modify "IN IP4 49.207.248.64" "IN IP4 192.168.1.200" rule 90 response ANY sdp-header Audio-Attribute modify "IN IP4 49.207.248.64" "IN IP4 192.168.1.200" rule 100 response ANY sdp-header Connection-Info modify "IN IP4 49.207.248.64" "IN IP4 192.168.1.200" rule 110 request ANY sdp-header mline-index 1 c= modify "IN IP4 49.207.248.64" "IN IP4 192.168.1.200" rule 120 response ANY sdp-header mline-index 1 c= modify "IN IP4 49.207.248.64" "IN IP4 192.168.1.200" rule 130 request ANY sdp-header Audio-Attribute modify "a=candidate:1 1 (.*) 49.207.248.64" "a=candidate:1 1 \1 192.168.1.200" rule 140 request ANY sdp-header Audio-Attribute modify "a=candidate:1 2 (.*) 49.207.248.64" "a=candidate:1 2 \1 192.168.1.200" rule 150 response ANY sdp-header Audio-Attribute modify "a=candidate:1 1 (.*) 49.207.248.64" "a=candidate:1 1 \1 192.168.1.200" rule 160 response ANY sdp-header Audio-Attribute modify "a=candidate:1 2 (.*) 49.207.248.64" "a=candidate:1 2 \1 192.168.1.200" rule 170 request ANY sdp-header Audio-Attribute modify "IN IP4 192.168.1.200" "IN IP4 49.207.248.64" ! voice class sip-profiles 299 rule 9 request ANY sip-header Via modify "SIP(.*) 192.168.1.200(.*)" "SIP\1 49.207.248.64\2" rule 10 request OPTIONS sip-header From modify "<sip:192.168.1.200" "<sip:cube.uccollabing.online" rule 20 request OPTIONS sip-header Contact modify "<sip:192.168.1.200" "<sip:cube.uccollabing.online" rule 30 request OPTIONS sip-header User-Agent modify "(IOS.*)" "\1\x0D\x0AX-MS-SBC: Cisco UBE/ISR4321/\1" rule 40 response ANY sdp-header Connection-Info modify "IN IP4 192.168.1.200" "IN IP4 49.207.248.64" rule 50 response ANY sdp-header Audio-Connection-Info modify "IN IP4 192.168.1.200" "IN IP4 49.207.248.64" ! ! ! ! voice class server-group 1 ipv4 172.16.0.160 description CUCM-SERVERS This section defines a server group for CUCM with the IP address 172.16.0.160 and the description 'CUCM-SERVERS'. ! voice class sip-options-keepalive 200 transport tcp tls sip-profiles 299 ! This section configures SIP OPTIONS keepalive with TCP and TLS transport, and applies SIP profile 299 for keepalive configuration. ! voice class tenant 200 handle-replaces localhost dns:cube.uccollabing.online session transport tcp tls no referto-passing bind control source-interface GigabitEthernet2 bind media source-interface GigabitEthernet2 pass-thru headers 290 no pass-thru content custom-sdp sip-profiles 200 sip-profiles 290 inbound early-offer forced block 183 sdp present ! This section configures tenant 200 with SIP-related settings, including session transport over TCP/TLS, and header passing configurations. It applies SIP profiles for both inbound and outbound traffic, forces early-offer, and blocks 183 SDP messages. ! ! voice translation-rule 1 rule 1 /\(#\)\(9180101010..\)/ /+\2/ ! voice translation-profile Teams-Outbound translate called 1 ! !Defines a translation rule to prepend "+" to the called number matching the pattern and applies it in the "Teams-Outbound" translation profile. voice translation-rule 2 rule 1 /^\+91\(.*\)/ /\1/ rule 2 // // voice translation-profile Remove-91 translate called 2 ! This configuration removes the +91 prefix from the called number for calls to India, using Rule 1 of the translation rules, and uses Rule 2 (no translation) as a fallback if no match is found. ! ip forward-protocol nd ip http server ip http authentication local ip http secure-server ip http secure-trustpoint CUBE-CERT-STORE ! ip route 0.0.0.0 0.0.0.0 192.168.1.1 dial-peer voice 201 voip description Outbound-To-Microsoft-Teams-P1 translation-profile outgoing Teams-Outbound preference 1 rtp payload-type comfort-noise 13 session protocol sipv2 session target dns:sip.pstnhub.microsoft.com:5061 destination e164-pattern-map 200 voice-class codec 1 voice-class sip tenant 200 voice-class sip options-keepalive profile 200 voice-class sip bind control source-interface GigabitEthernet2 voice-class sip bind media source-interface GigabitEthernet2 dtmf-relay rtp-nte srtp fax protocol none no vad ! Configures an outbound dial-peer to Microsoft Teams (P1) with SIP protocol, codec preferences, SRTP, and DTMF relay. Uses translation profile Teams-Outbound and binds control/media to GigabitEthernet2 dial-peer voice 202 voip description Outbound-To-Microsoft-Teams-P2 translation-profile outgoing Teams-Outbound preference 2 rtp payload-type comfort-noise 13 session protocol sipv2 session target dns:sip2.pstnhub.microsoft.com:5061 destination e164-pattern-map 200 voice-class codec 1 voice-class sip tenant 200 voice-class sip options-keepalive profile 200 voice-class sip bind control source-interface GigabitEthernet2 voice-class sip bind media source-interface GigabitEthernet2 dtmf-relay rtp-nte srtp fax protocol none no vad !Similar to dial-peer 201, but for a different Teams endpoint (P2). It shares the same settings with the previous dial-peer. dial-peer voice 203 voip description Outbound-To-Microsoft-Teams-P3 translation-profile outgoing Teams-Outbound preference 2 rtp payload-type comfort-noise 13 session protocol sipv2 session target dns:sip3.pstnhub.microsoft.com:5061 destination e164-pattern-map 200 voice-class codec 1 voice-class sip tenant 200 voice-class sip options-keepalive profile 200 voice-class sip bind control source-interface GigabitEthernet2 voice-class sip bind media source-interface GigabitEthernet2 dtmf-relay rtp-nte srtp fax protocol none no vad !Similar to dial-peer 202, but for Teams P3. The same settings apply, ensuring all Teams connections are handled similarly. ! dial-peer voice 3 voip description inbound Inbound-From-Teams rtp payload-type comfort-noise 13 session protocol sipv2 incoming uri to 290 voice-class codec 1 voice-class sip tenant 200 dtmf-relay rtp-nte srtp no vad !Configures an inbound dial-peer from Teams, specifying the URI for inbound calls to go to 290, with SRTP and DTMF relay. ! dial-peer voice 100 voip description Inbound-From-CUCM session protocol sipv2 session transport udp incoming uri via CUCM voice-class codec 1 voice-class sip bind control source-interface GigabitEthernet1 voice-class sip bind media source-interface GigabitEthernet1 dtmf-relay rtp-nte no vad !Configures an inbound dial-peer from CUCM using SIP over UDP. It also specifies codec and DTMF settings. ! dial-peer voice 101 voip description Outbound-To-CUCM translation-profile outgoing Remove-91 rtp payload-type comfort-noise 13 session protocol sipv2 session transport udp session server-group 1 destination e164-pattern-map 1 voice-class codec 1 voice-class sip bind control source-interface GigabitEthernet1 voice-class sip bind media source-interface GigabitEthernet1 dtmf-relay rtp-nte no vad ! !Outbound dial-peer to CUCM with similar settings as dial-peer 1, but it binds to server-group 1 and uses the e164-pattern-map 1. ! sip-ua no remote-party-id retry invite 2 xfer target dial-peer connection-reuse crypto signaling default trustpoint CUBE-CERT-STORE handle-replaces ! ! This section configures the SIP user agent settings, including retry behavior, call transfer handling, signaling encryption, and reuse of SIP connections.
Configuration on CUCM
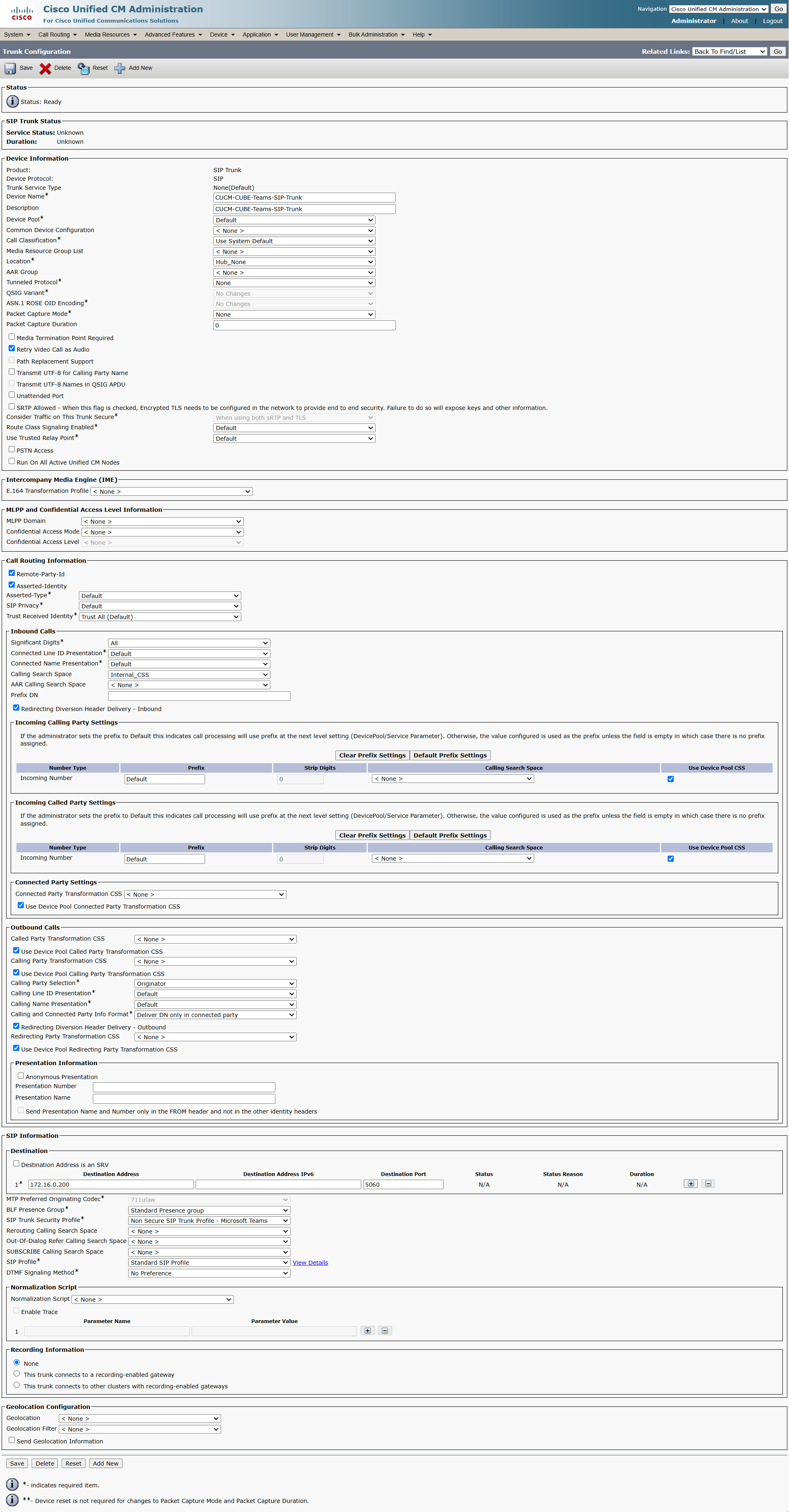
Below is the SIP Trunk on CUCM pointing to Cisco CUBE for Direct Routing to MS Teams
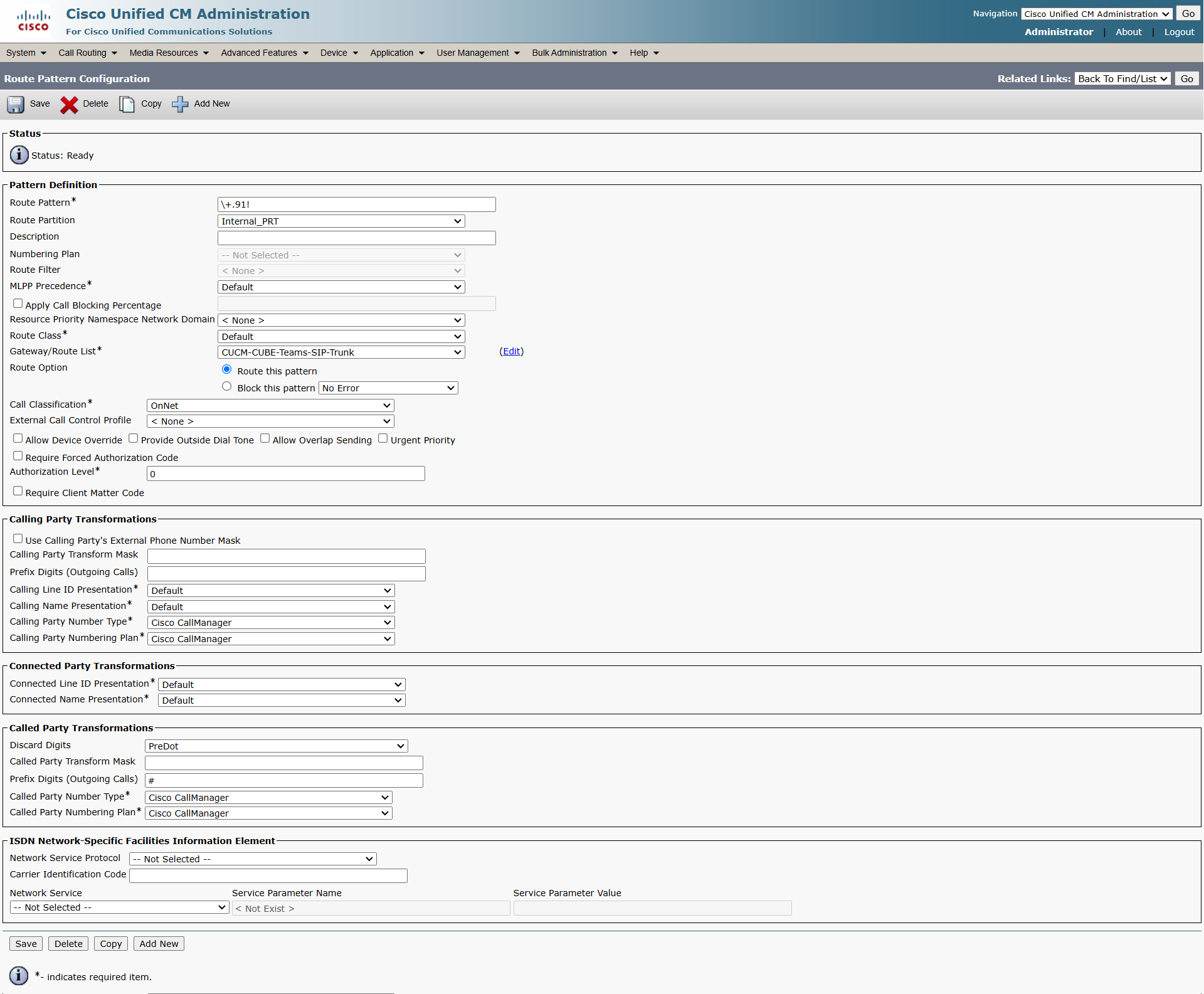
Below is the Route Pattern pointing to Microsoft Teams via Cisco CUBE
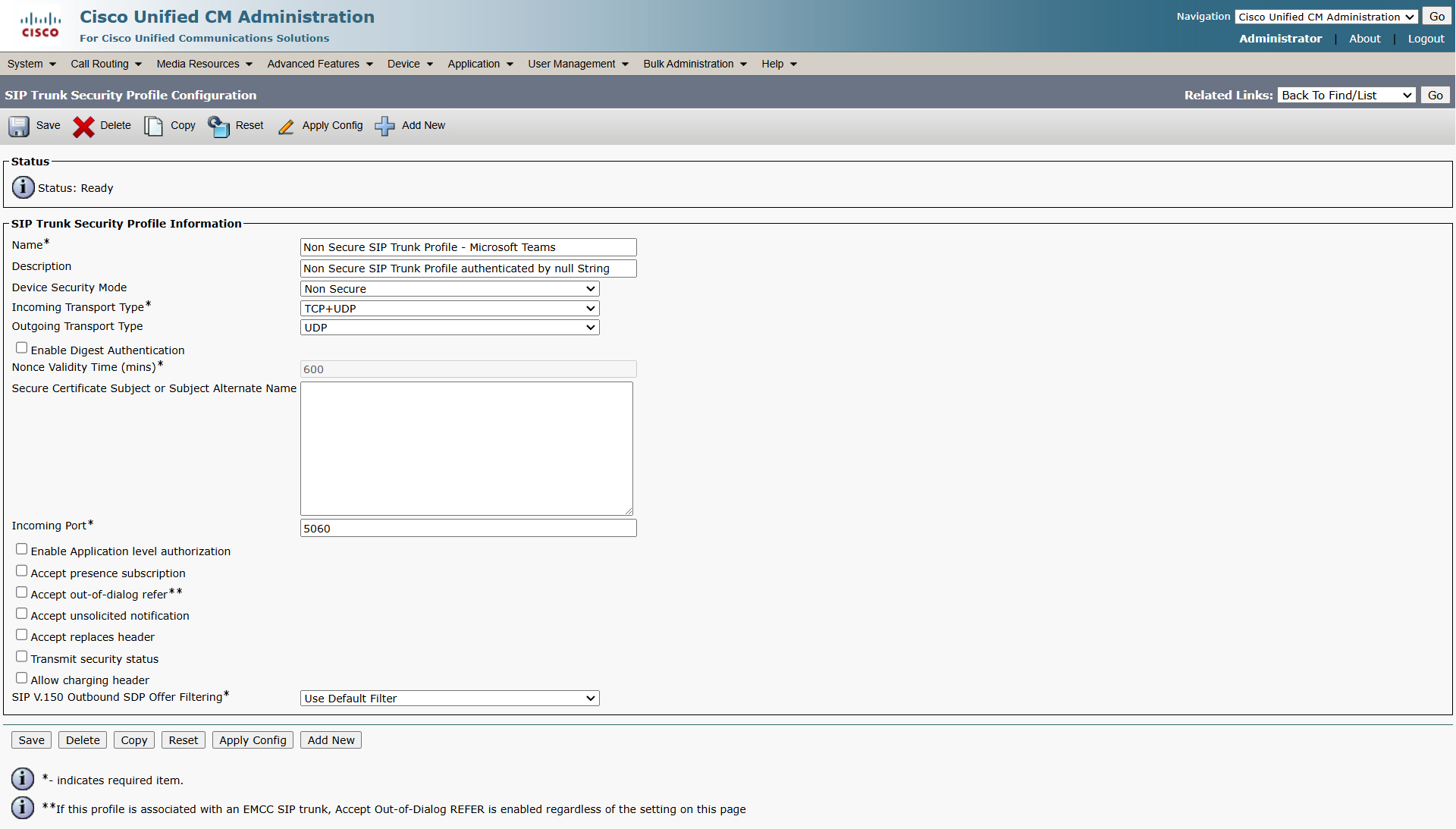
Below is the SIP Trunk Security Profile used by the SIP Trunk
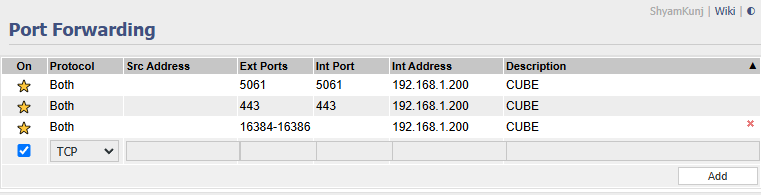
Port Forwarding on Wifi Router
YouTube Video: Step-by-Step Guide to Direct Routing with Microsoft Teams Using Cisco CUBE SBC

I am working in an IT company and having 10+ years of experience into Cisco IP Telephony and Contact Center. I have worked on products like CUCM, CUC, UCCX, CME/CUE, IM&P, Voice Gateways, VG224, Gatekeepers, Attendant Console, Expressway, Mediasense, Asterisk, Microsoft Teams, Zoom etc. I am not an expert but i keep exploring whenever and wherever i can and share whatever i know. You can visit my LinkedIn profile by clicking on the icon below.
“Everyone you will ever meet knows something you don’t.” ― Bill Nye